Cain & Abel is a password recovery tool for Microsoft Operating Systems. It allows easy recovery of various kind of passwords by sniffing the network, cracking encrypted passwords using Dictionary, Brute-Force and Cryptanalysis attacks,
recording VoIP conversations, decoding scrambled passwords, recovering wireless network keys, revealing password boxes, uncovering cached passwords and analyzing routing protocols. The program does not exploit any software vulnerabilities or bugs that could not be fixed with little effort. It covers some security aspects/weakness present in protocol’s standards, authentication methods and caching mechanisms; its main purpose is the simplified recovery of passwords and credentials from various sources, however it also ships some “non standard” utilities for Microsoft Windows users.
recording VoIP conversations, decoding scrambled passwords, recovering wireless network keys, revealing password boxes, uncovering cached passwords and analyzing routing protocols. The program does not exploit any software vulnerabilities or bugs that could not be fixed with little effort. It covers some security aspects/weakness present in protocol’s standards, authentication methods and caching mechanisms; its main purpose is the simplified recovery of passwords and credentials from various sources, however it also ships some “non standard” utilities for Microsoft Windows users.
STEP 1) DOWNLOAD THE SOFTWARE “CAIN AND ABEL”
here is the link DOWNLOAD
DOWNLOAD ( mirror )
STEP 2) INSTALL AND START IT.
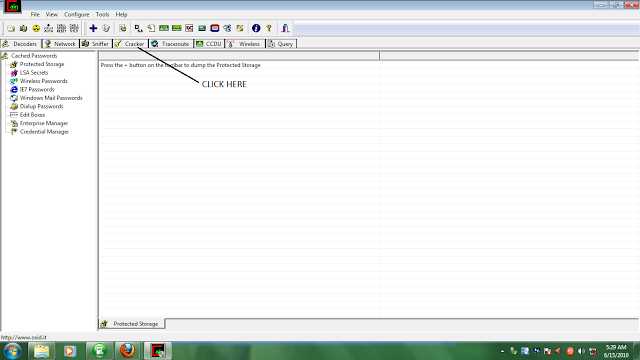
STEP 3) CLICK ON THE CRACKER TAB
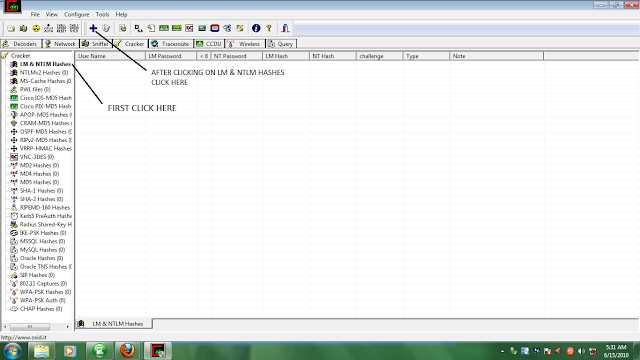
STEP 4) IN THE SIDEBAR CLICK ON “LM & NTLM HASHES” OPTION AND THEN CLICK ON THE POSITIVE SIGN.
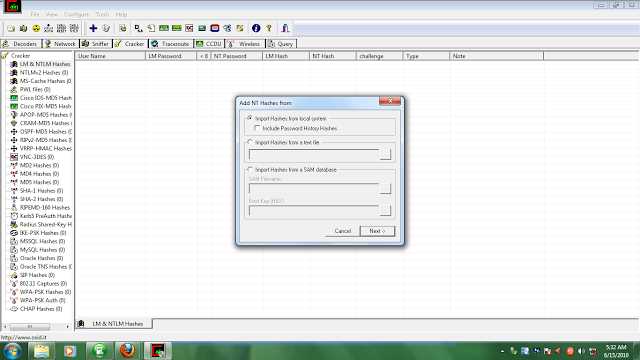
STEP 5) THEN A WINDOW APPEARS SELECT “IMPORT HASHES FROM LOCAL SYSTEM” OPTION AND THEN CLICK NEXT.
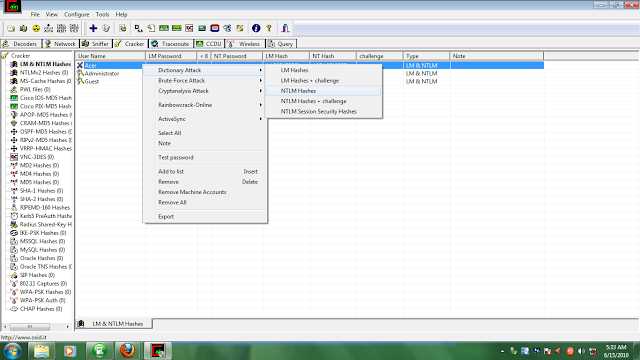
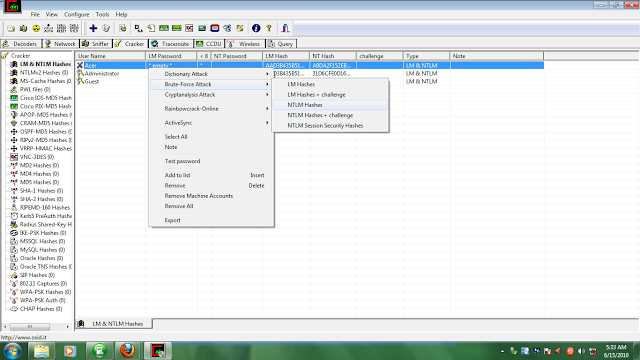
STEP 6) RIGHT CLICK THE OPTION WHICH REMAINS AFTER EXCLUDING THE ADMINISTRATOR AND GUEST OPTION AND THEN CLICK ON DICTIONARY ATTACK
AND THEN ON NTLM HASHES (it will check all dictionary words for the password).
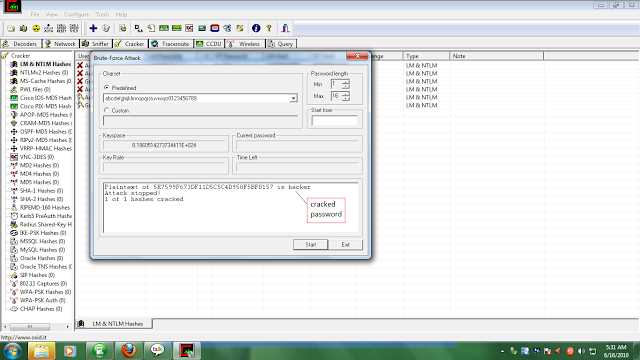
STEP 7) IF THE PASSWORD IS NOT CRACKED BY DICTIONARY ATTACK SELECT BRUTE FORCE ATTACK AND THEN NTLM HASHES.
*HERE IS THE RESULT*